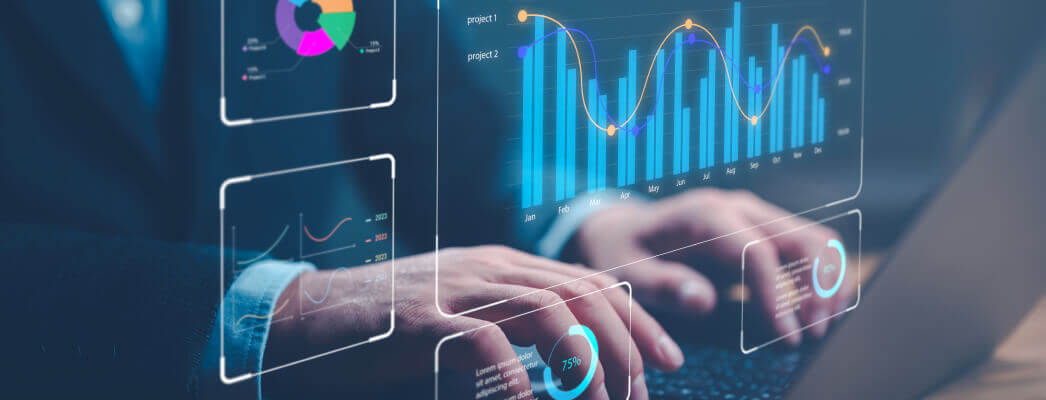
An Intelligent and Secure Restaurant Management System
We hear your concerns and direct you to opt for the very best suited services and solutions for your hospitality business. With CIS, you can run your restaurant the way you intend it and focus on what matters the most. Our team makes sure our customers get the most exceptional possible services without exceeding their funding as expected and meeting all deadlines in a timely fashion. We design the restaurant POS, that is tailored to satisfy your specific and unique needs. Our restaurant management system is bound to suit your business in the best way possible and also addresses the most beneficial practices likely.
Request Free ConsultationExplore Our Achievements
With our robust strategy and top-notch customer service, we have significantly increased our business results and are recognized worldwide.
-
10 B+
Client Revenues -
12+
Successful Years -
1000+
IT Ninjas -
5000+
Projects
features
features
Range of innovative features for Restaurant Management Software
Easy to use menu management system gives you the flexibility to manage the menu as per the varied needs of your guests. You can categorize your restaurant menu into various groups and subgroups smoothly. Manually editing your menu is also possible with our customizable menu management feature. You can easily create seasonal combo meals packs for various occasions. It enables you to design a distinct menu for special events, seasons or even days with customization for the most minute details. Impress your guests with fantastically arranged menus.

Range of innovative features for Restaurant Management Software
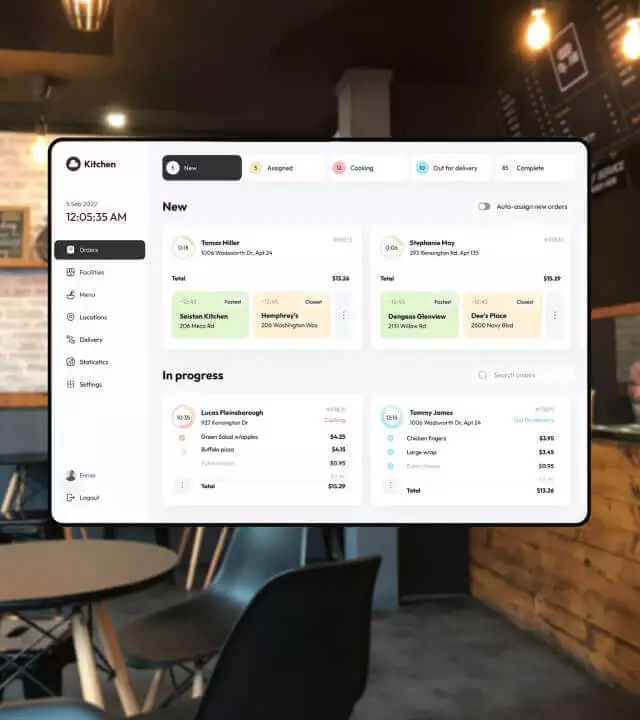
The Table Management feature lets you perform the best practice of your restaurant tools. It permits you to monitor your table requests by the graphical representation of the design of your restaurant. With these representations, it gets quite simple for the servers to deliver prompt service. Additionally, it lets you manage each table at your restaurant's status. You can mark tables that are to be served promptly, and which are unattended or unoccupied. This gives you a comprehensive picture of the serving situation of your restaurant right on your dashboard.

Range of innovative features for Restaurant Management Software
A Restaurant operates efficiently with the co-operation and collaboration of a lot of people. Our Restaurant POS Software solution allows you to divide jobs for your staff to make sure that it continues to be so. You can easily restrict the access of customers in your Restaurant Management System. Your team will have access to the only sections that are delegated to them. You can give guest users entry separately. You can willingly share or restrict the accessibility in compliance with your requirements. It provides your restaurant with a well-administered and secure arrangement.

Range of innovative features for Restaurant Management Software
Our Restaurant management system provides a detailed analysis of the parameters of your restaurant within just a few seconds. You can customize the accounts sync according to your needs. No matter what information you require from the system; be it the most profitable days or the best selling dishes - you receive all the data you need using our detailed reports to make better business decisions. Besides, it enables you to monitor staff activities to guarantee the smooth operation of your restaurant.